Mobile Device Expert
Upgrades both the hardware and the software as and when required. Identify, diagnose, and either repair or orchestrate the repair of problems with the mobile device hardware, application software, and software. Within an MDM environment, you can manage the application allocations for each device.
This is quickly growing, its applications are becoming more varied over time, and it is progressively displacing other comparable communication options available on the market, like landlines and post offices. The evolution of mobile technology from a primary phone and texting device to a multi-tasking device that can be used for GPS navigation, internet browsing, gaming, and instant messaging, among other things, is impressive. According to experts, the growth of wireless networking and mobile computing is essential to the future of computer technology.
Mobile technology usage
- The proliferation of smartphone technology in commercial settings has been beneficial to telecollaboration. People can connect from any location using mobile technology and acquire the papers and documents that are required to complete collaborative work.
- The nature of employment is shifting due to the rise of mobile technology. Workers are no longer confined to their workstations but can perform their jobs anywhere.
- Using mobile technology, your company can realise significant time and financial savings. Workers who routinely perform their duties from home can save thousands of dollars. The use of mobile phones obviates the requirement for more costly technology, such as the services provided by telephone providers.
- Cloud-based applications are typically less expensive than their traditional counterparts. Your company’s adaptability and effectiveness could benefit from implementing technology.
- Technology that can be used on mobile devices can significantly boost workplace productivity.
- Implementing mobile applications results in an average reduction of 7.5 hours per week in labour expenses incurred by staff. Using mobile devices in the workplace, such as cell phones and other portable electronic devices, can help employees improve their productivity.
- In recent years, cloud-based services have become highly prevalent worldwide. It has been determined that mobile applications that use the cloud are more beneficial than smartphone applications, particularly regarding the amount of storage capacity they offer.
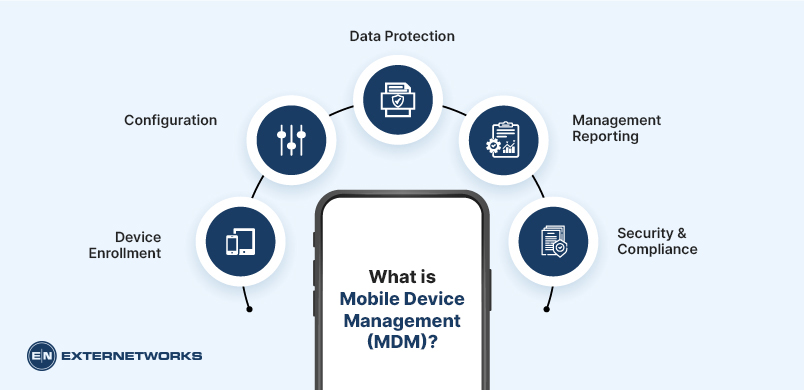
How Does Mobile Device Management Work?
The MDM server, housed in a data center, and an MDM agent are two essential elements of mobile device administration. (located on the mobile device). The IT administrator must enter the new policy in the MDM server’s administration console whenever they want to set up and distribute guidelines to any mobile device connected to the corporate network. The command is then implemented on the mobile device using the built-in APIs of the device after the server pushes the update to the MDM agent.
Mobile Device Management has changed over time. Scalability was a problem initially, but central remote administration has done away with antiquated procedures like SIM cards and client-initiated updates. Today’s top MDM solutions can instantly identify new devices when they connect to a corporate network and implement simple configuration rules from a single admin dashboard to all connected devices.
Organisations can monitor and control mobile devices thanks to various mobile device management products available on the market. Among these methods’ key characteristics are the following:
- Device inventory and monitoring
- Management and assistance on the go
- To accept or reject proposals
- Regulation of passcodes
- Remote control of services
- Alerts to signal users trying to use jailbreaking to bypass restrictions
Is Mobile Device Management Necessary?
In recent years, many businesses have adopted the standard practice of using mobile devices to watch business applications and platforms, participate in voice or video calls, and access business networks.
Mobile Device Management solutions are a secure investment that you should prioritise if your workers use mobile devices to access your company’s data or files. One lost or stolen mobile gadget with network access could cause serious security problems. Without an MDM solution’s security, a lost device could compromise private data (such as customer credit card numbers or confidential medical information), resulting in expensive fees and lawsuits for compliance violations.
More workers than ever are choosing to work from home instead of in corporate offices, using a much wider variety of devices. Employees will require constant access to company information and software. As a result, there is a particular security danger to corporate data. To safeguard their business devices, we advise organisations with many mobile devices—particularly those handling sensitive data—to consider mobile device management solutions.
Protect your smartphone from hackers:
As both a parent and a professional, I’ve put together some things you can do to protect your smartphone from hackers to protect your personal and professional life:
- Add extra protection with your face, fingers, pattern or PIN: First, the basics. Locking your phone with Face ID, fingerprint, pattern or pin is your primary defense, especially if your phone is lost or stolen. (Options vary by device, operating system, and manufacturer.) Take it further for even better protection. Protect your phone accounts with strong passwords and use two-factor authentication for apps that offer it, doubling your line of defense.
- Use a VPN: In other words, don’t jump on public Wi-Fi networks unprotected. A VPN hides your connection from hackers, allowing you to connect privately on unsecured public networks in airports, coffee shops, hotels, etc. With a VPN connection, you know that your sensitive data, documents, and activities are safe from prying eyes, which is certainly a great feeling considering how much personal and professional business we conduct on our smartphones.
- Use official stores for your apps: Both Google Play and Apple’s App Store have measures to prevent potentially harmful programs from entering the stores. Malicious apps are often found outside of app stores. They can run in the background and compromise your personal information like passwords, credit card numbers and more – basically anything you store on your phone. Also, carefully check app descriptions and app store reviews before downloading. Malicious apps and fakes can still find their way into the stores, and here are some ways to prevent these nasty apps from entering your phone.
- Back up your phone data: Backing up your phone is always a good idea for two reasons: First, it makes the transition to a new phone easier by transferring the backup data from the old phone to the new phone. Second, it ensures your data stays with you if your phone is lost or stolen. This way, you can erase the data from your lost or stolen phone while keeping a safe copy of the data in the cloud. iPhone and Android phones have easy ways to back up your phone regularly.
- Learn how to lock or wipe your phone in an emergency remotely: In the worst case, your phone is lost. Gone. Whether it is hopelessly lost or stolen. What now, Lock it remotely or even wipe the data completely. Brushing your phone one last time may seem like a drastic step, but if you back up regularly, as mentioned above, your data will be safe in the cloud – ready for recovery. This means that hackers cannot access sensitive information about you or your business, which can keep you out of trouble and protect your professional business. Apple provides a detailed guide for iOS users to wipe their devices remotely, and Google also provides a guide for Android users.
- Remove old programs and update the remaining programs: We all download apps, use them once and then forget they’re on our phones. Take a moment to swipe through the screen to see which ones you’ve finished and delete them along with their data. Some apps have an account associated with them that can also store data on your phone. Take the extra step and delete these accounts to erase all data off your phone. This is because each additional app is another app that needs to be updated or may have a security issue. During data breaches and vulnerabilities, it makes sense to remove old programs. As a matter of fact, I update them regularly and enable automatic updates when possible. Updates bring new features to apps and often fix security issues.
- Protect your phone: If a large part of your life is on your phone, installing security software on it can protect you and the things you keep on your phone. Whether you’re an Android or iOS owner, mobile security software can keep your data, purchases and payments safe.
- 8 Common Sense Tips to Protect Your Smartphone: From locking your smartphone with a pin to installing a security app, these common sense tips will help protect you and your data.
Here are eight tips to improve the security of your smartphone and the information stored on it:
- Avoid revealing personal information: A text message that appears to be from someone else’s bank may be different. If you receive a request for account information from a business via email or text message, please contact the business directly to confirm the request. The same advice applies to clicking on links in unsolicited emails or text messages.
- Lock your phone with a PIN, password or pattern: Setting it up is easy. On most Android™ devices, you can get instructions about location and security settings. iOS users can find these features in the General Settings section of their settings.
- Only download apps from trusted stores: If you’re looking for a new game or something more productive, use places like Google Play™. Be sure to check the ratings and reviews when available, and read the app’s privacy policy to see exactly what features your phone will have when you download it.
- Data Backup: This is more about protecting and restoring data in a disaster. Back up your contacts, music, photos, videos and documents to the cloud with Backup Assistant Plus and Verizon Cloud.
- Keep your operating system and applications updated: Both usually receive updates from time to time that add new features and provides improved security.
- Log out of websites after payment: If you go to a bank or store with your smartphone, log out of these websites after completing the transaction. Other tips include not saving usernames and passwords on your phone and avoiding incidents when using a public Wi-Fi network.
- Turn off Wi-Fi and Bluetooth® when not in use: You think they’re a way to connect to something, but thieves can use them to connect to your device and access your files.
- Protect your investment: Losing your smartphone can be pretty stressful. 200,000 devices are lost, stolen or damaged every day. You may be surprised at the high off-contract price when your lost smartphone is replaced with a similar make and model.
How to know if your phone is hacked
Here are the most common signs that your phone is hacked:
- You notice something you don’t recognize on your phone: See apps you still need to download or text messages you have. Undelivered, purchases you didn’t make and suspicious phone calls.
- Your phone is running slowly: In addition to being abnormally slow, your phone is consuming more resources and battery and getting hotter than usual. Malware running in the background can significantly reduce its effectiveness.
- Mysterious data usage spikes: Data usage spikes can occur without any changes. Malicious processes can consume your mobile data in the background while you monitor your activities.
- Strange behavior: Applications don’t work as they should, start and shut down unexpectedly, or crash and won’t load.
- Pop-ups: If you notice a lot of pop-ups on your screen, you may have spyware or malware.
Conclusion:
Cell phones have ushered in an entirely new period of technology. They have unquestionably contributed to improving people’s quality of life regarding their communication ability. However, the adverse effects of mobile phones and the distractions they cause are responsible for many hazardous and unhealthy situations.